IP Monitoring for a Safer Internet

The digital landscape has undergone a massive transformation in just the last decade. Cloud computing has become an essential component in the world of technology, and the Internet of Things (IoT) is rapidly weaving its tendrils into every facet of our lives.
While these advancements offer immense convenience and efficiency, they also pose unexplored cybersecurity challenges. In this complex ecosystem, IP address monitoring emerges as a critical line of defense, safeguarding our data and devices from the ever-evolving threats lurking in the shadows.
Cloud Security Trends: A Shifting Landscape
Businesses of all sizes, across industries, are packing their bags and heading for the cloud, leaving behind the dusty confines of on-premises infrastructure. This migration isn’t just a fad; it’s a shift driven by a potent cocktail of trends reshaping the way we work and operate.
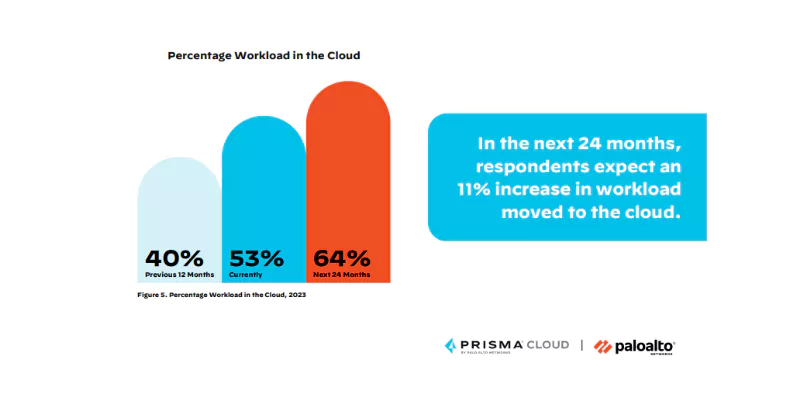
[Source]
The cloud’s seemingly boundless scalability and accessibility come at a cost: increased attack surface.
According to a recent comprehensive report, 65% of organizations experienced cloud security incidents in 2023 alone. These breaches often exploit vulnerabilities in misconfigured cloud environments or compromised user credentials.
Here are some common cloud security threats in 2023:
- Phishing: Luring users to reveal credentials or click malicious links through emails, texts, or fake websites.
- Misconfigurations: Unsecured cloud storage buckets, open APIs, and overly permissive access controls offer easy entry points.
- Account hijacking: Compromised user credentials grant attackers access to sensitive data and systems.
- Denial-of-service (DoS) attacks: Overwhelming cloud resources with traffic to disrupt service and extort funds.
- Supply chain attacks: Exploiting vulnerabilities in third-party software or services used by cloud providers.
- Cryptojacking: Hijacking cloud resources to mine cryptocurrency without the owner’s consent.
- Ransomware: Encrypting critical data and demanding payment for decryption, crippling operations.
- Insider threats: Malicious actors within an organization abusing privileged access to steal data or sabotage systems.
- Data breaches: Exfiltrating sensitive information like customer data or financial records.
- Unpatched vulnerabilities: Exploiting known weaknesses in cloud software or misconfigurations.
As the cloud continues to permeate every aspect of business, effective IP address monitoring becomes an essential tool for identifying suspicious activity and preventing unauthorized access.
IoT Network Monitoring: Securing the Evolving Frontier
From smart homes and wearables to connected cars and industrial machinery, IoT devices are rapidly transforming every aspect of our lives. According to a study, by 2028, the market is projected to have grown significantly and be worth USD 355686.12 million.
Here’s why they’re becoming so popular:
- Convenience and Automation: Imagine never having to adjust your thermostat or turn on lights again. IoT devices automate tasks and anticipate our needs, making life easier and more efficient.
- Enhanced Experiences: Track your fitness goals with real-time data, monitor your home’s security remotely, or personalize your entertainment experience – IoT devices unlock a world of possibilities.
- Data-Driven Insights: The data collected by IoT devices can be analyzed to gain valuable insights, improve decision-making, and optimize operations in various sectors.
- Innovation and Growth: The IoT market is booming, driving innovation in fields like artificial intelligence, sensor technology, and connectivity, creating new job opportunities and economic growth.
The rise of IoT is just the beginning. As devices become more affordable, connected, and intelligent, we can expect even more transformative experiences and a truly interconnected world in the years to come.
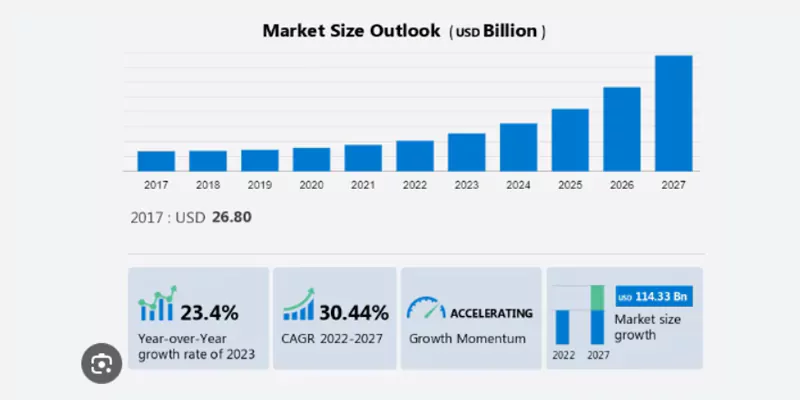
[Source]
The explosive growth of IoT devices, from smart homes to industrial sensors, presents a new breed of security challenges.
These often resource-constrained devices can harbor vulnerabilities, making them prime targets for cybercriminals seeking to launch botnet attacks or steal sensitive data.
To understand the importance of IP address monitoring for IoT and securing connected devices, imagine this: You have a smart home filled with connected devices, from your trusty refrigerator to your baby monitor.
Each device has a unique IP address, just like a home address, that identifies it on the network. IP address monitoring acts like a watchful eye, observing the traffic flowing to and from each device, constantly checking for suspicious activity.
Here’s why IP address monitoring is essential for IoT security:
- Enhanced Visibility: It provides a clear picture of all devices connected to your network, even those hidden behind firewalls or with limited computing power.
- Threat Detection: By analyzing data traffic patterns and identifying anomalies, IP address monitoring can detect suspicious activities like malware infections, unauthorized access attempts, or botnet infiltration before they escalate into full-blown attacks.
- Improved Device Management: Monitoring IP addresses helps you track the health and performance of individual devices.
- Compliance and Security: Effective IP address monitoring demonstrates compliance with data privacy regulations and industry standards, showcasing your commitment to securing sensitive information.
Implementing IP address monitoring tools for IoT network monitoring allows for real-time visibility into device activity, enabling administrators to detect and isolate compromised devices before they can wreak havoc.
Effective IP Address Management: The Foundation of Security
With the sheer number of IP addresses in play, due diligence in IP address management is paramount.
Unassigned or unused IP addresses can become open doors for attackers to exploit. Implementing automated discovery and tracking tools ensures that all devices within a network are accounted for and monitored, leaving no blind spots for malicious actors. Additionally, leveraging GeoIP databases to identify the location of connecting devices can further enhance threat detection capabilities.
Adapting to Emerging Cyber Threats With Awakish
The cyberthreat landscape is constantly evolving, with new vulnerabilities and attack vectors emerging seemingly overnight. To stay ahead of the curve, organizations must adopt a proactive approach to IP address monitoring.
Imagine a world where your smart home isn’t just convenient, but impenetrable. Where every connected device, from your fridge to your baby monitor, is shielded from prying eyes and malicious actors. That’s the promise of Awakish!
By weaving Awakish IP address monitoring into the fabric of your security strategy, you can ensure that your connected devices remain bastions of security in the face of ever-evolving cyber threats.
Get in touch with Awakish now to safeguard your IoT and cloud networks!



