Just as medieval fortifications controlled the flow of people and goods, port monitoring controls the digital traffic, scrutinizing every packet that seeks entry.
Understanding the significance of cyber threats and port security is crucial and employing effective strategies for network protection while implementing robust gateway security measures is essential to building a fortified digital fortress.
Port monitoring stands guard at the gateways of modern networks, making it necessary when cyber attacks are becoming ever-sophisticated.
The Looming Threat
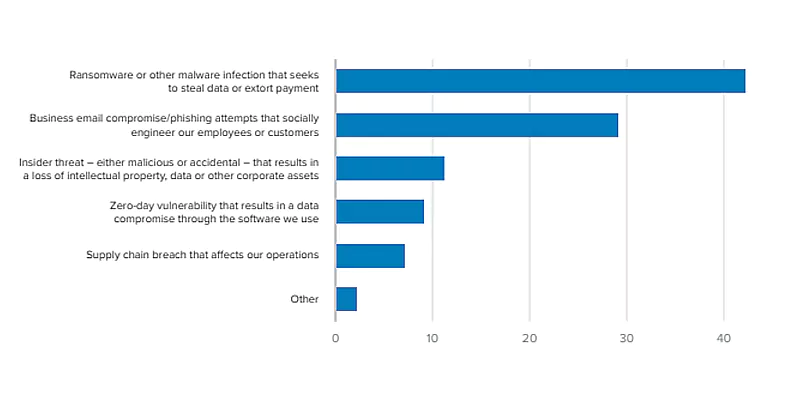
The global threat landscape is rife with malicious actors, constantly honing their tools and devising novel ways to breach network defenses. Cyber threats come in various forms, from targeted attacks by evolving hacking groups to opportunistic exploits by botnets and script kiddies.
[Source]
These threats often exploit vulnerabilities in open or improperly secured ports, making port monitoring a critical line of defense.
According to an esteemed prediction, ransomware attacks alone are expected to cost businesses $265 billion globally by 2026.
Strategies for Effective Network Protection
1.Know Your Network:
The first step in effective port monitoring is understanding your network landscape. Conduct a thorough inventory of all devices and applications, map their associated Ports, and identify authorized services running on each. This creates a baseline against which anomalous activity can be readily identified.
2.Implement Port Control Measures:
Once you understand your network, it’s time to take control. Close all unused Ports, restrict access to critical Ports, and implement granular access control policies to limit communication channels for specific devices and applications. This significantly reduces the attack surface and makes it harder for malicious actors to find exploitable entry points.
3.Monitor and Analyze Network Traffic:
Continuous port monitoring is key to staying ahead of threats. Utilize robust tools that provide real-time insights into traffic patterns, identify suspicious activity, and flag potential intrusions. Analyze logs and alerts diligently to detect anomalies and investigate suspicious connections promptly.
4.Embrace the Power of Automation:
Modern port monitoring solutions offer sophisticated automation capabilities, allowing you to automate routine tasks like port scanning, vulnerability scans, configuration checks, and incident response procedures. This frees up valuable time for security teams to focus on complex investigations and strategic threat mitigation.
5.Stay Informed and Proactive:
The cybersecurity landscape is dynamic, and staying abreast of the latest threats and vulnerabilities is crucial. Regularly update your port monitoring tools and security solutions, invest in ongoing security awareness training for your staff, and actively participate in threat intelligence communities to stay ahead of the curve.
Importance of Port Scanning in Cybersecurity

Port scanning is a fundamental tool in the port monitoring arsenal. It allows you to actively identify open Ports, assess their associated services, and uncover potential vulnerabilities. Regular port scanning helps you proactively address security gaps and close unauthorized Ports before they become vulnerable access points for attackers.
Gateway Security Measures
Firewalls and intrusion detection/prevention systems (IDS/IPS) are crucial Gateway Security Measures that work in tandem with port monitoring. These systems enforce policy-based access control, filter incoming and outgoing traffic based on established rules, and detect and block malicious activity at the network perimeter. By layering these defenses with robust port monitoring, you create a multi-layered security posture that significantly enhances network defense.
Safeguard your network with Awakish
In today’s digitally connected world, port monitoring is no longer an optional luxury; it’s a fundamental necessity.
By actively monitoring and controlling Ports, implementing effective network protection strategies, and leveraging advanced gateway security measures, organizations can safeguard their valuable assets from the ever-growing threat landscape. Remember, a secure network is a resilient network, and port monitoring is the vigilant watchdog that keeps it that way.
Awakish port monitoring tools offer unparalleled network security, setting the standard for robust network defense. Elevate your cybersecurity and run your organization in peace. Choose Awakish for the best protection. Sign up now!



